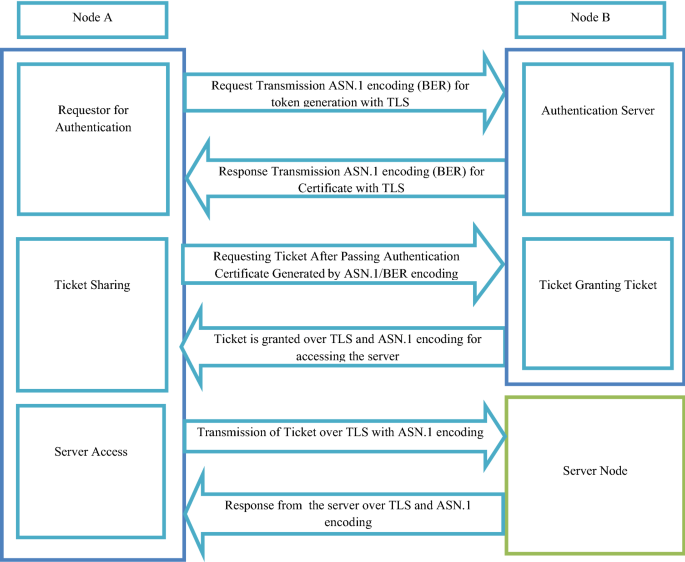
The sequences of authentication, authorization and transmission data... | Download Scientific Diagram

Processes for authentication and confidentiality of mobile voice and... | Download Scientific Diagram
RPC: if a request doesn't include an authentication header, don't increment the bruteforce counter · Issue #1554 · transmission/transmission · GitHub

H1EAX series" High-capacity and highly accurate module | Finger Vein Authentication Modules for Embedding in Devices | Products and Solutions | Hitachi Industry & Control Solutions, Ltd.

PCI Requirement 8.2.1 – Use Strong Cryptography to Render All Authentication Credentials Unreadable During Transmission and Storage

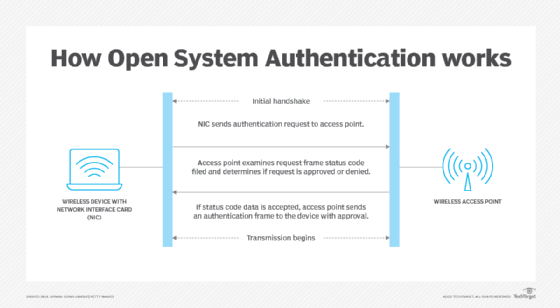
Linksys Official Support - What are Authentication Types, Basic Rate and Transmission Rate and how to Enable or Disable them

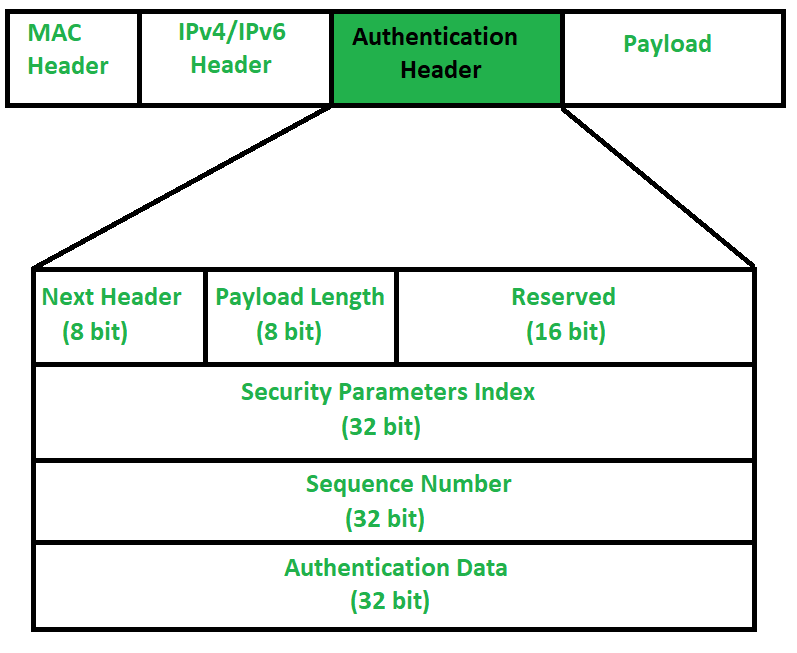
Securing Data Transmission and Authentication. Securing Traffic with IPSec IPSec allows us to protect our network from within IPSec secures the IP protocol. - ppt download

A flow diagram of client-aware secure data transmission methods. The... | Download Scientific Diagram

What is navigation message authentication? - Inside GNSS - Global Navigation Satellite Systems Engineering, Policy, and Design

Female hand with mobile phone withdrawing money from atm using NFC contactless wi-fi pay pass system. Wireless authentication and data transmission s Stock Photo - Alamy

Linksys Official Support - What are Authentication Types, Basic Rate and Transmission Rate and how to Enable or Disable them

Configuring Layer 2 Transparent Transmission of 802.1X Authentication Packets - S1720, S2700, S3700, S5700, S6700, S7700, and S9700 Series Switches Common Operation Guide - Huawei

Symmetry | Free Full-Text | Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN